The best free Android apps of 2023: the best apps in the Google Play Store
The best free Android apps, tested and ranked

Finding the best free android apps on the Google Play Store can be a real chore, what with all the options out there. Who knew, when Google launched Android 13 years ago, that there would be this many available apps to choose from. You can find one to cater for every need, whim, or desire. And, a lot of them come with that magic price tag, free, so that you’re just a few clicks away from taking your phone to the next level.
But, just because there’s such a glut of apps out there doesn’t mean that most of them are quality. There’s a lot that you should probably skip. In fact, the Play Store gives you a lot of tools to parse through all the noise, from Editor’s Picks for different categories to recommendations for new releases or for apps based on your prior downloads.
You can also narrow the search by reading reviews and ratings or searching for an app you have and seeing what similar results pop up.
With that said, there are so many in the store’s library, that a free android app that’s worth downloading can still get lost in the shuffle. To help you find the best android apps that are free, we’ve collected our top picks here to make sure you have all the apps you could want or need on your phone or tablet, sorted into categories so you can more easily find what you're looking for.
Not an Android user? You can use these apps on one of the best Android emulators.
- These are the world's very best Android phones
- What's the best phone of 2023?
- Stay safer online with an Android VPN app
Best new free Android app
Why you can trust TechRadar
Every few weeks we add a new app to this list, and you'll find the latest addition below.
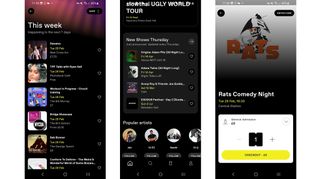
DICE: Live Shows
DICE: Live Shows is potentially the one and only app you’ll need to find and book live shows of all kinds, from gigs to comedy nights, festivals, life drawing, and various workshops.
Give DICE access to your location and it will display things that are happening nearby, but you can also search for specific artists, locations, dates, and prices.
Clever tools like the ability to sync your music streaming app for personalized recommendations help DICE stand out, and you can also stream online shows, invite and follow friends, save events for later if you’re not ready to book yet, and join waiting lists if events have sold out.
You can also buy tickets from within the app, and get refunds on them or transfer them to a friend if needed. So it’s a slick, well thought out app, that has pretty much every feature you could reasonably ask for when hunting out and booking shows.
Current page: Best new free Android app
Next Page The best free art and design apps for AndroidGet daily insight, inspiration and deals in your inbox
Get the hottest deals available in your inbox plus news, reviews, opinion, analysis and more from the TechRadar team.
James is a freelance phones, tablets and wearables writer and sub-editor at TechRadar. He has a love for everything ‘smart’, from watches to lights, and can often be found arguing with AI assistants or drowning in the latest apps. James also contributes to 3G.co.uk, 4G.co.uk and 5G.co.uk and has written for T3, Digital Camera World, Clarity Media and others, with work on the web, in print and on TV.

