After the T-Mobile breach, companies are preventing customers from securing their accounts
We take a deep-dive into the aftermath of the T-Mobile breach

T-Mobile’s most recent data breach leaked the personal information of 53 million people, with names, addresses and even social security numbers leaked online.
Those affected face not only the risk of identity theft, but also the growing threat of SIM-swapping that can allow attackers to hijack their online accounts.
While security experts have given consumers advice about how to protect themselves, some well known companies are actively preventing them from securing their accounts.
- We’ve built a list of the best security keys on the market
- Check out our list of the best identity theft protection available
- And the best password managers around
SIM-swaps
In a SIM-swap, criminals steal their victim’s phone number by convincing the mobile carrier to transfer the victim’s phone service to a SIM-card that they control.
The T-Mobile breach makes it easier for criminals to do this because it leaked answers to questions the mobile carrier might ask before agreeing to switch the victim’s SIM.
“In a hypothetical scenario, if customer service asks an attacker for the last four digits of your social security number and credit card in order to access your account, the attacker can now correctly answer those challenges,” notes Kevin Lee, a security researcher and PhD student in the computer science department at Princeton University.
“Once inside, the attacker can ask the customer service agent to update the SIM card on your account to a new one in his possession, which will essentially divert all your incoming calls and messages … to the attacker.”
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
As many online accounts allow users to reset their passwords and receive two factor authentication (2FA) codes via SMS, once an attacker steals a user’s phone number they can also hijack their online accounts. Security experts have advised those affected by the T-Mobile breach to protect their accounts by enabling non-SMS based 2FA methods, such as authentication apps or security keys. But not all companies give their users this option and even when they do, many still have vulnerabilities in the way they authenticate their users, putting customer accounts at risk.
Companies are putting their customers at risk
Last year, Lee and a team of researchers warned many well-known companies about these vulnerabilities in how they authenticate their users.
Venmo, the mobile payment app, is one of the companies they contacted. A Venmo user can request a password reset via SMS and will also receive 2FA codes via SMS — they do not have the option to use a more secure method such as an authenticator. This means that if a user is SIM-swapped the attacker has everything they need to hijack their victim’s Venmo account and take control of their money.
WordPress.com is another offender Lee and his colleagues contacted. Like Venmo, they allow users to reset their password via SMS. Unlike Venmo they allow users to set up an authenticator, but require users to receive 2FA codes via SMS as a backup, completely undermining the security benefits of the authenticator.
If a WordPress.com user is SIM-swapped the attacker can reset their password and bypass the need for an authenticator by having a code sent via SMS, allowing them to hijack their victim’s account and take over their websites.
WordPress.com’s situation is made worse by the fact that there is no indication in a user’s 2FA settings that when an authenticator is set up, SMS is enabled as a backup. In my account, for example, it tells me “You've enabled two-step authentication on your account — smart move! When you log in to WordPress.com, you'll need to enter your username and password, as well as a unique passcode generated by an app on your mobile device.” If I scroll down, I can see my backup methods, but SMS is not listed. It’s only when I go to log in that I see SMS is provided as a backup option.
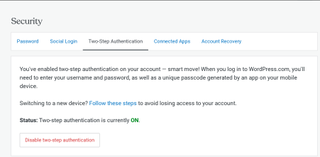
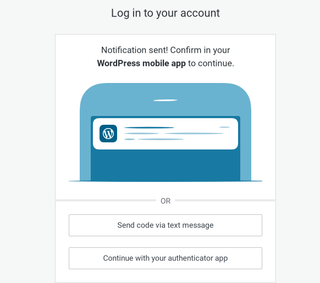
Overall Lee and his colleagues identified 17 websites that were putting their customers’ accounts at risk of hijacking after a SIM-swap. Only 4 of the 17 fixed the issue.
Venmo and WordPress.com are among the 13 that failed to take any action, as I confirmed by testing with my own accounts and contacting customer service. In some cases, companies did not take action because they did not understand that the way they were authenticating users was insecure, which Lee described as “concerning.” Others recognized the problem, he said, but opted not to make changes “for fear of inconveniencing customers.”
What companies can do
Companies don’t have to take drastic measures to protect their customers’ accounts from hijacking after a SIM-swap.
Lee emphasized the importance of threat modeling, a process in which companies analyze potential ways for an attacker to interact with their site in order to identify vulnerabilities and fix them ahead of time.
A few of the more secure sites they analyzed had presumably engaged in threat modeling and had themselves identified the problem with allowing password resets and 2FA codes to be sent via SMS.
These companies “would disallow SMS-authenticated recovery for accounts that had SMS 2-step login enabled,” Lee said. This provides at least some protection if a user is SIM-swapped, as the attackers won’t be able to gain access to the victim’s account unless they have also obtained their password through other means.
Lee and his colleagues also recommended companies give their customers at least one secure 2FA option, like an authenticator app or security key.
As they highlighted, these options are not just more secure, but allow for quicker authentication and can be used without an internet connection.
Lee emphasized via email that mandating SMS 2FA as a backup “might not fit everyone’s security needs, and could even be hurting users,” especially when it is done without their knowledge. He added that “transparency is crucial,” and that companies need to provide users with clear information about the methods they can use to access their account.
That way at least a user who has an authenticator set up won’t be blindsided if they are SIM-swapped and find their account is still hijacked because SMS 2FA was silently enabled as a backup.
Companies that continue to do nothing, however, are helping cybercriminals, not their customers.
- Stay secure online with the best endpoint protection around
Rebecca Morris is a freelance writer based in Minnesota. She writes about tech, math and science.

